Crosschq Blog
How to Identify Fake Interview Candidates: Your Complete Video Detection Guide

It takes as little as 70 minutes for someone with no image manipulation experience to create a fake interview candidate that could pass for a real person on a video interview, according to cybersecurity firm Palo Alto Networks. Even more alarming? Around 17% of hiring managers have already encountered fake interview candidates using deepfake technology.
If you're responsible for hiring, this comprehensive guide will arm you with the knowledge, techniques, and strategies to identify fake candidates in video interviews before they infiltrate your organization and cause devastating consequences.
What Are Fake Interview Candidates?
Fake interview candidates are job applicants who misrepresent their true identity, qualifications, or intentions during the hiring process. In 2025, this phenomenon has evolved far beyond simple resume embellishment into sophisticated deception involving:
- AI-generated personas with completely fabricated identities
- Deepfake technology that masks the candidate's real appearance
- Proxy interviewing where one person interviews but another shows up for work
- Stolen identities combined with AI-altered photos and videos
These aren't just harmless imposters—they represent serious security, financial, and operational threats to organizations of all sizes.
The Explosive Growth of Fake Candidate Interviews
The numbers are staggering and growing exponentially:
Current State of the Crisis
By 2028, 1 in 4 job candidates worldwide will be fake, according to research and advisory firm Gartner. But the crisis is already here:
- 17% of hiring managers have encountered candidates using deepfake technology in video interviews
- Out of 827 applications for one software developer position, about 100 were attached to fake identities (that's 12.5%)
- 95% of résumés received by some startup founders are from impostors pretending to be Americans
The Remote Work Factor
"Remote jobs unlocked the possibility of tricking companies into hiring fake candidates," said Dawid Moczadlo, co-founder of data security software company Vidoc Security Lab. The shift to remote interviewing has created unprecedented opportunities for sophisticated fraud.
Financial and Security Impact
When fake candidates are successfully hired, the consequences are severe:
- $6.8 million in overseas revenue generated by North Korean impostors hired by over 300 U.S. companies
- National security risks when workers from sanctioned nations gain access to sensitive systems
- Data theft, malware installation, and corporate espionage once imposters gain internal access
How to Identify Fake Candidates in Video Interviews: The Complete Detection Framework
Protecting your organization requires a multi-layered approach combining technology, behavioral analysis, and strategic verification techniques.
Visual Detection Techniques
Facial Movement Analysis
What to watch for:
- Unnatural facial expressions that seem slightly out of sync with speech
- Inconsistencies around the eyes and mouth where deepfake technology often fails
- Rigid or limited head movements that suggest video manipulation
- Edge blurring or glitching when the candidate moves quickly
Pro tip: Ask candidates to turn their face to the side or move their head in different directions. Deepfake technology struggles with profile views and rapid movements.
Real-Time Verification Tests
The hand test: Ask candidates to place their hand in front of their face. This simple request can immediately expose deepfake fraud, as AI filters often fail when objects obstruct the face.
Dynamic gestures: Request specific movements like:
- Touching their nose with their finger
- Showing both hands simultaneously
- Standing up and sitting down
- Adjusting their camera position
Audio Detection Indicators
Voice Pattern Analysis
Red flags to listen for:
- Audio-visual lag where voice doesn't align perfectly with lip movements
- Unnatural voice cadence or robotic speech patterns
- Background noise inconsistencies that suggest audio manipulation
- Sudden audio quality changes during the interview
Response Pattern Recognition
Behavioral indicators:
- Delayed responses to unexpected questions as if processing before playback
- Inability to adapt to follow-up questions or requests for clarification
- Overly perfect answers that sound scripted or generated
- Reluctance to engage in spontaneous conversation
Technical Environment Assessment
Connection and Setup Analysis
Warning signs:
- Not logged into any email address during the video call
- Suspicious IP addresses that don't match claimed locations
- Multiple applications running that could indicate assistance tools
- Refusal to share screen or show their workspace
Camera and Video Quality
Detection points:
- Inconsistent video quality throughout the interview
- Unusual lighting changes that suggest video manipulation
- Reluctance to adjust camera angles or show different views
- Filters or effects that can't be removed when requested
Advanced Strategies for Fake Candidate Interview Detection
Multi-Stage Verification Process
Pre-Interview Identity Verification
- Government ID verification with live gesture confirmation
- LinkedIn profile validation checking for AI-generated photos and engagement history
- Reference preliminary checks before the formal interview process
- Skills assessment completion under controlled conditions
During Interview Protocols
- Mandatory camera-on policy throughout the entire interview
- Multiple interview rounds with different team members to ensure consistency
- Technical skill demonstrations that require real-time problem-solving
- Behavioral question deep-dives that require specific, personal examples
Post-Interview Validation
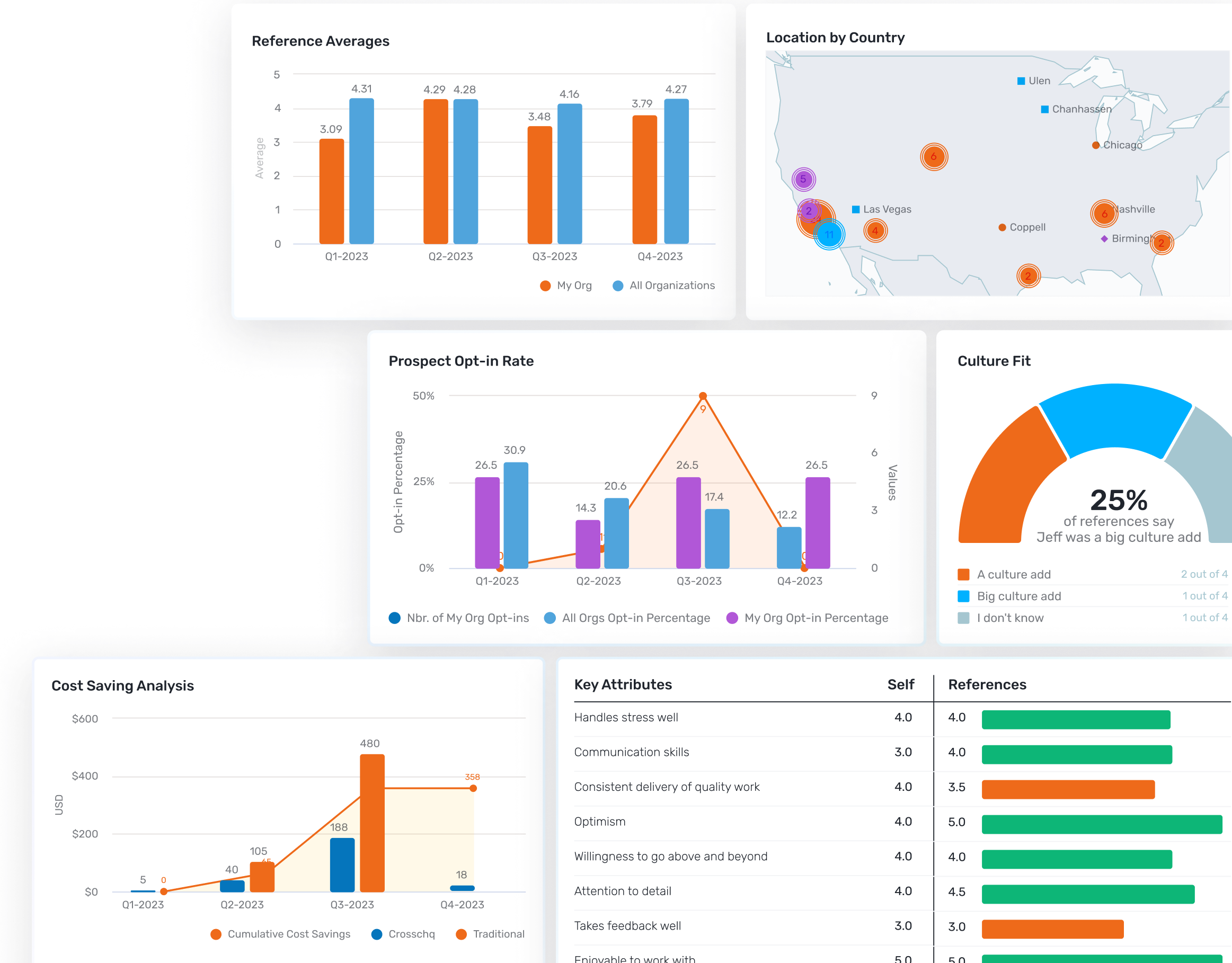
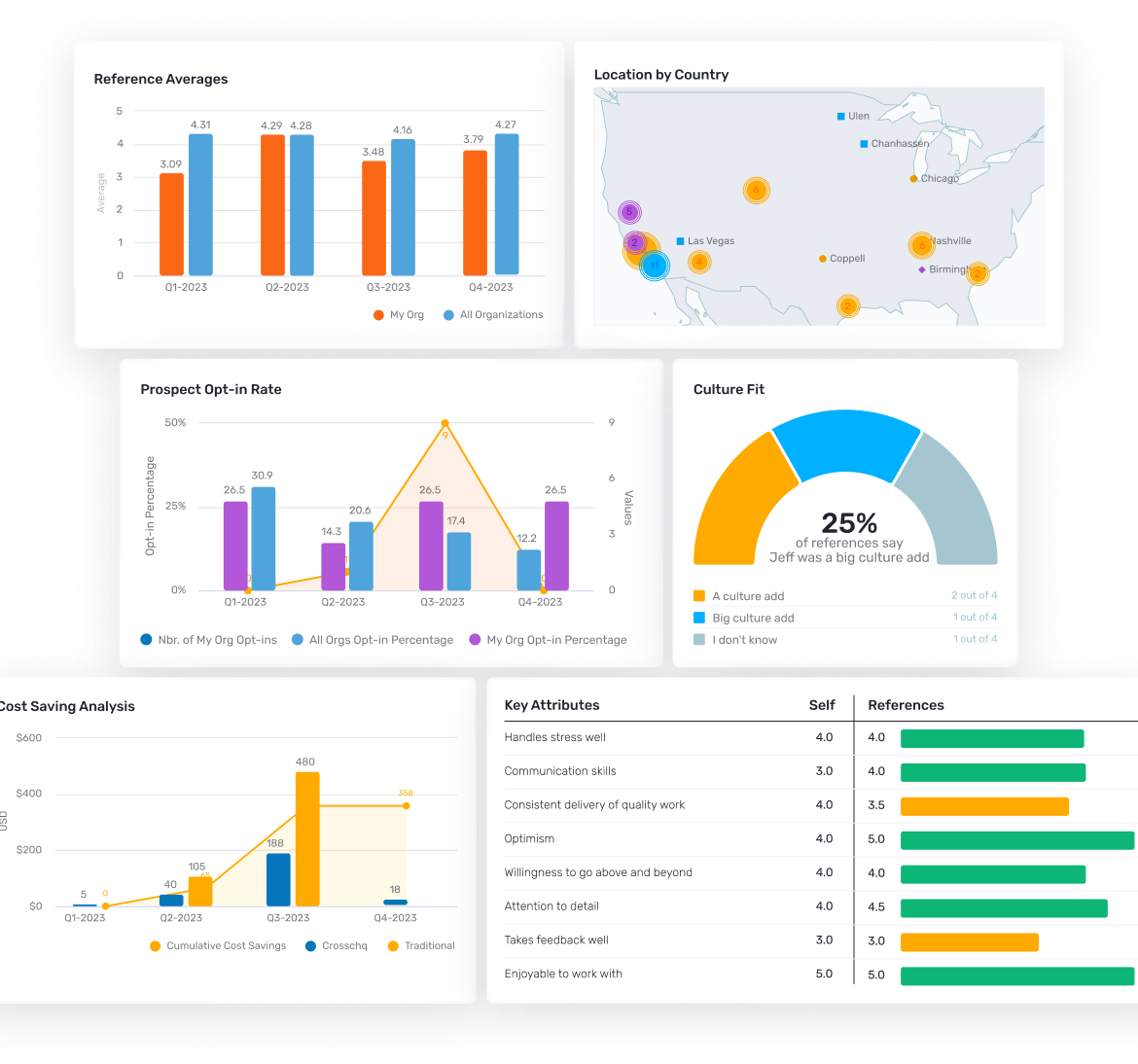
- Comprehensive reference checking using Crosschq's 360 digital reference platform
- IP address analysis to verify claimed locations
- Interview recording review for inconsistencies missed during live conversation
- Background check integration to verify all claimed credentials
Industry-Specific Detection Approaches
Technology Sector Protection
The tech industry faces the highest risk of fake candidates, particularly for remote roles. Implement these additional measures:
- Live coding assessments that can't be pre-prepared
- System architecture discussions requiring deep, practical knowledge
- Real-time problem-solving scenarios that test authentic expertise
- Team collaboration simulations to assess genuine interpersonal skills
Healthcare and Finance Safeguards
Given the critical nature of these industries, extra verification is essential:
- Professional license verification through official channels
- Case study discussions requiring specific clinical or financial expertise
- Regulatory knowledge testing that can't be easily researched during interviews
- Ethics scenario evaluation to assess genuine professional judgment
Red Flags That Immediately Identify Fake Candidate Interviews
Immediate Disqualifiers
These behaviors should trigger immediate investigation:
- Refusal to turn on video or persistent "technical difficulties"
- Inability to perform simple verification gestures when requested
- Dramatic inconsistencies between application materials and interview performance
- Suspicious reference patterns with multiple contacts sharing IP addresses
- Generic responses to specific, technical questions requiring personal experience
Subtle Warning Signs
These indicators require deeper investigation:
- Perfect but impersonal answers that lack authentic detail
- Reluctance to discuss specific workplace scenarios or personal experiences
- Inconsistent knowledge depth across related skill areas
- Unusual interview scheduling requirements or communication patterns
- Vague or evasive responses to follow-up questions requiring elaboration
Geographic and Logistical Red Flags
- IP addresses that don't match claimed locations
- Time zone inconsistencies in communication patterns
- Background elements that contradict claimed residence
- Currency or cultural references that don't align with stated background
Technology Solutions for Detecting Fake Interview Candidates
AI-Powered Detection Systems
Leading organizations are deploying sophisticated tools:
- Real-time deepfake detection that analyzes video feeds during interviews
- Voice authentication technology that identifies synthetic speech patterns
- Behavioral biometric analysis that tracks typing patterns and interaction styles
- Comprehensive fraud alerting that flags suspicious patterns immediately
Integration with Existing Systems
Modern fraud detection integrates seamlessly with hiring workflows:
- ATS integration that provides fraud alerts within existing platforms
- Automated reporting that tracks fraud attempts across the organization
- Reference verification systems that detect coordinated fake testimonials
- Compliance monitoring that ensures all detection methods meet legal requirements
Crosschq's Comprehensive Fraud Detection
Crosschq's advanced fraud detection capabilities provide industry-leading protection:
- Same IP address detection across multiple references or candidates
- Device fingerprinting to identify coordinated fraud attempts
- Behavioral pattern analysis that spots suspicious reference activities
- Real-time fraud alerting during the reference checking process
Building a Fraud-Resistant Interview Process
Pre-Interview Foundation
Candidate Verification Protocol
- Identity documentation requirements with live verification
- Professional credential validation through official channels
- Social media presence authentication to identify AI-generated profiles
- Reference check implementation before investing interview time
Communication Standards
- Official email requirements for all candidate correspondence
- Video call platform security with recording capabilities
- Standardized interview scheduling that prevents manipulation
- Clear fraud detection disclosure to deter potential imposters
Interview Execution Best Practices
Environmental Control
- 360-degree workspace verification before interviews begin
- Lighting and audio quality assessment to identify manipulation
- Background authenticity checks to verify claimed locations
- Device and connection analysis to detect suspicious setups
Dynamic Questioning Strategies
- Unprepared scenario discussions that require real experience
- Follow-up question cascades that test knowledge depth
- Personal experience validation through specific detail requests
- Cultural and contextual questions that verify claimed backgrounds
Post-Interview Verification
Comprehensive Validation
- Interview recording analysis by multiple team members
- Reference check completion using advanced digital platforms
- Background check integration for comprehensive verification
- Team consensus requirements before making offers
Documentation and Compliance
- Detailed fraud detection documentation for legal protection
- Decision-making audit trails that justify hiring choices
- Legal compliance maintenance throughout the process
- Continuous improvement tracking to refine detection methods
Legal and Ethical Considerations in Fake Candidate Detection
Privacy and Consent Requirements
When implementing fraud detection measures:
- Obtain explicit consent for interview recording and monitoring
- Provide transparency about fraud detection methods being used
- Maintain GDPR compliance in all verification processes
- Respect candidate privacy while ensuring organizational security
Documentation Standards
- Detailed record-keeping of all fraud detection activities
- Clear decision rationale when fraud is suspected
- Legal review processes for handling confirmed fraud cases
- Audit trail maintenance for compliance and legal protection
Avoiding Discrimination
- Standardized detection protocols applied equally to all candidates
- Objective verification criteria that don't discriminate based on demographics
- Cultural sensitivity in verification requirements
- Bias prevention measures in fraud detection processes
Industry-Specific Vulnerability Assessment
High-Risk Sectors
Technology Companies
Why they're targeted: Remote work prevalence, high-value data, system access Additional protection needed:
- Live technical demonstrations
- System security verification
- Code review capabilities
- Architecture knowledge testing
Financial Services
Why they're targeted: Access to financial data, regulatory compliance requirements Additional protection needed:
- Regulatory knowledge assessment
- Ethics scenario evaluation
- Compliance history verification
- Financial crime awareness testing
Healthcare Organizations
Why they're targeted: Patient data access, critical system control Additional protection needed:
- Medical license verification
- Patient care scenario discussions
- HIPAA compliance understanding
- Clinical knowledge validation
Medium-Risk Industries
- Government contractors: Security clearance implications
- Education institutions: Student data protection concerns
- Legal services: Client confidentiality requirements
- Manufacturing: Intellectual property protection needs
Future-Proofing Your Organization Against Fake Candidates
Emerging Threat Preparation
As AI technology advances, new threats will emerge:
- Real-time deepfake improvements requiring more sophisticated detection
- Voice cloning advancement making audio verification more challenging
- Behavioral AI development that can mimic human interaction patterns
- Coordinated fraud networks using multiple fake identities simultaneously
Technology Investment Strategy
Stay ahead of evolving threats:
- Regular fraud detection tool updates to match advancing AI capabilities
- Staff training programs on new fraud identification techniques
- Industry collaboration to share threat intelligence
- Continuous process refinement based on new fraud patterns
Organizational Resilience Building
- Cross-functional fraud prevention teams including HR, IT, and security
- Regular fraud simulation exercises to test detection capabilities
- Vendor security assessment for hiring technology providers
- Incident response planning for confirmed fraud cases
Measuring and Improving Your Fake Candidate Detection
Key Metrics to Track
- Fraud detection rate: Percentage of fake candidates identified
- False positive rate: Legitimate candidates incorrectly flagged
- Detection speed: How quickly fraud is identified in the process
- Cost per detection: Resources invested in fraud prevention
Continuous Improvement Process
- Regular detection method review based on new threat intelligence
- Team training updates incorporating latest fraud techniques
- Technology capability assessment to ensure adequate protection
- Process refinement based on lessons learned from attempts
Success Measurement
- Reduced hiring fraud incidents compared to previous periods
- Improved Quality of Hire through better candidate verification
- Enhanced team confidence in the hiring process integrity
- Stronger organizational security posture overall
Take Immediate Action: Protect Your Organization Today
The threat of fake interview candidates is real, sophisticated, and growing rapidly. Every day you delay implementing comprehensive fraud detection measures increases your organization's vulnerability to devastating consequences.
Start with these critical steps:
- Audit your current interview process for fraud detection gaps
- Implement basic verification requirements for all video interviews
- Train your hiring team on fake candidate identification techniques
- Deploy advanced fraud detection technology integrated with your existing systems
Essential Immediate Protections
- Mandatory government ID verification with live gesture confirmation
- Camera-on requirements throughout all video interviews
- Dynamic verification tests including the hand-over-face request
- Comprehensive reference checking with fraud detection capabilities
Long-Term Security Strategy
- Investment in AI-powered detection tools that evolve with threats
- Regular team training updates on emerging fraud techniques
- Industry collaboration to share threat intelligence
- Continuous process improvement based on new fraud patterns
The cost of prevention is minimal compared to the devastating impact of successfully hiring a fake candidate. Don't wait until your organization becomes another cautionary tale.
Ready to build an impenetrable defense against fake interview candidates? Explore Crosschq's comprehensive fraud detection solutions and see how industry leaders protect their hiring processes while improving Quality of Hire.
Take the Guesswork
Out of Hiring
Schedule a demo now
%20-200x43.png)





