FRAUD DETECTION
ApplicantX: End-to-end candidate fraud defense
Verify identity, surface résumé manipulation, spot AI/deepfakes, and validate references—powered by proprietary detection models and a global hiring threat database.
.png)
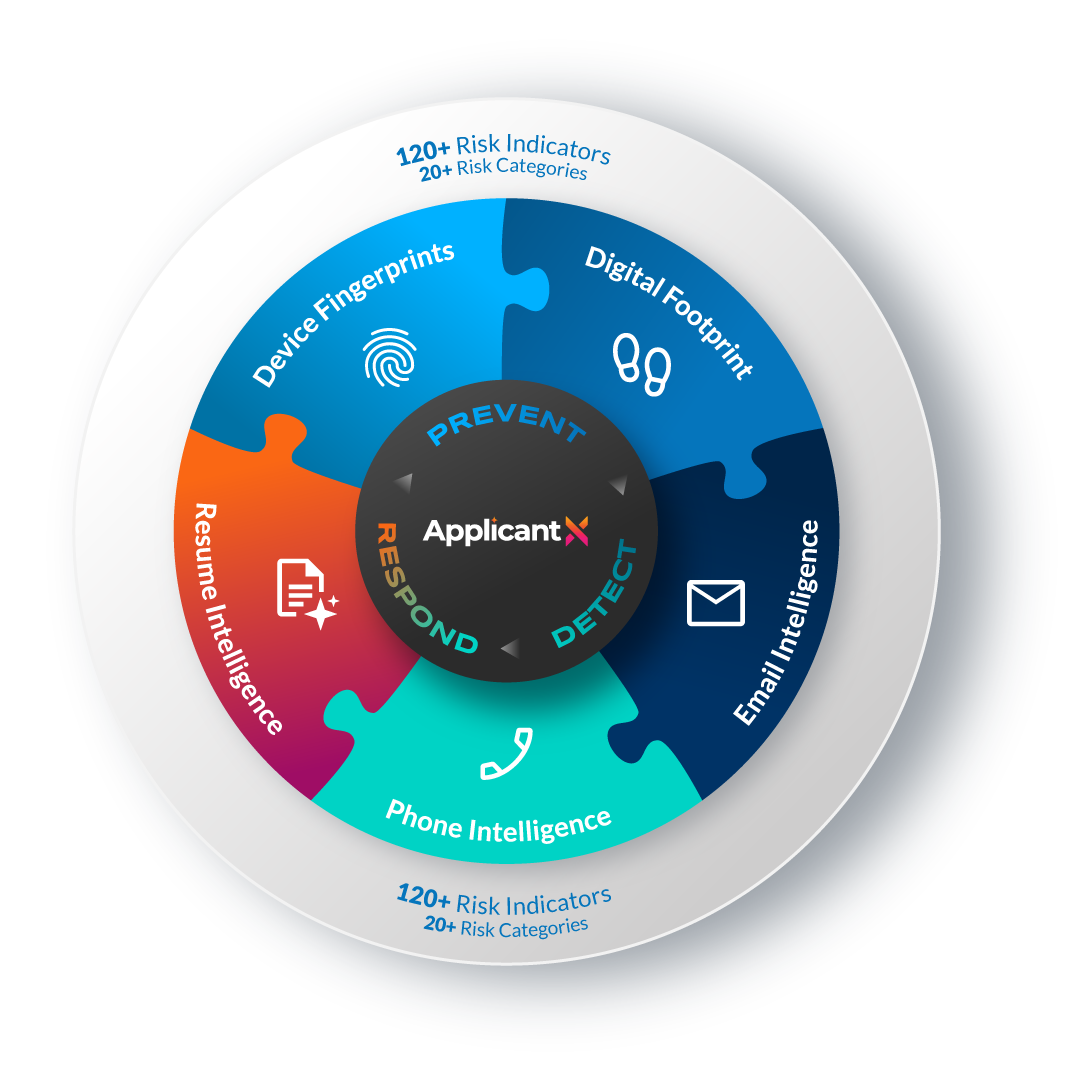
INTELLIGENT FRAUD RISK DETECTION — WHEREVER YOU HIRE
Instantly evaluate key candidate identifiers — name, email, phone, LinkedIn, and résumé — to uncover hidden risks. Receive a data-driven fraud score and context that help your team verify authenticity faster and make smarter hiring decisions.
Driven by Multi-Signal Detection
Multi-Signal Analysis
The engine scans digital presence, contact details, and resume patterns to detect anomalies and identity mismatches.
Unified Fraud Risk Score
Each candidate is scored in real-time on a Low-High continuum, reflecting overall trust level and risk indicators.
Instant Integration
Access fraud insights directly through the API so every screening workflow can instantly validate candidate credibility.
VERIFY RÉSUMÉ INTEGRITY—AUTOMATICALLY
Identify AI-written or copy-pasted content, inflated titles, and other resume red flags — then verify claims against trusted sources. Behavioral signals flag mass applications and unusual patterns so high-risk profiles don’t slip through.

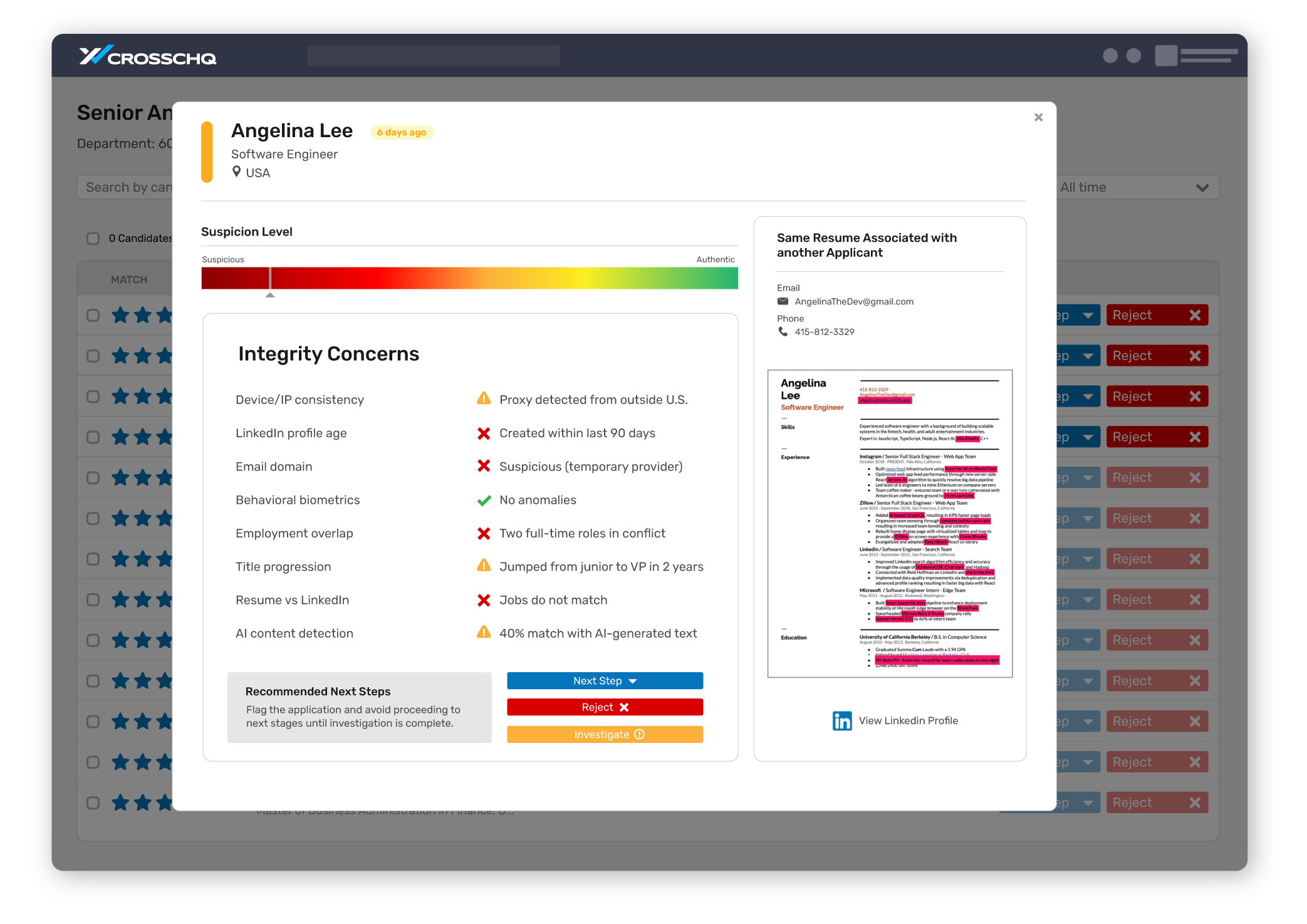
From résumé to reliable signal
AI text forensics
OCR + LLM spot generated or pasted blocks, reuse, and “strategic embellishment.”
Role & timeline checks
Compare titles, dates, and claims against verified employment and education.
Behavior risk signals
Flag burst application activity and pattern anomalies in real time.
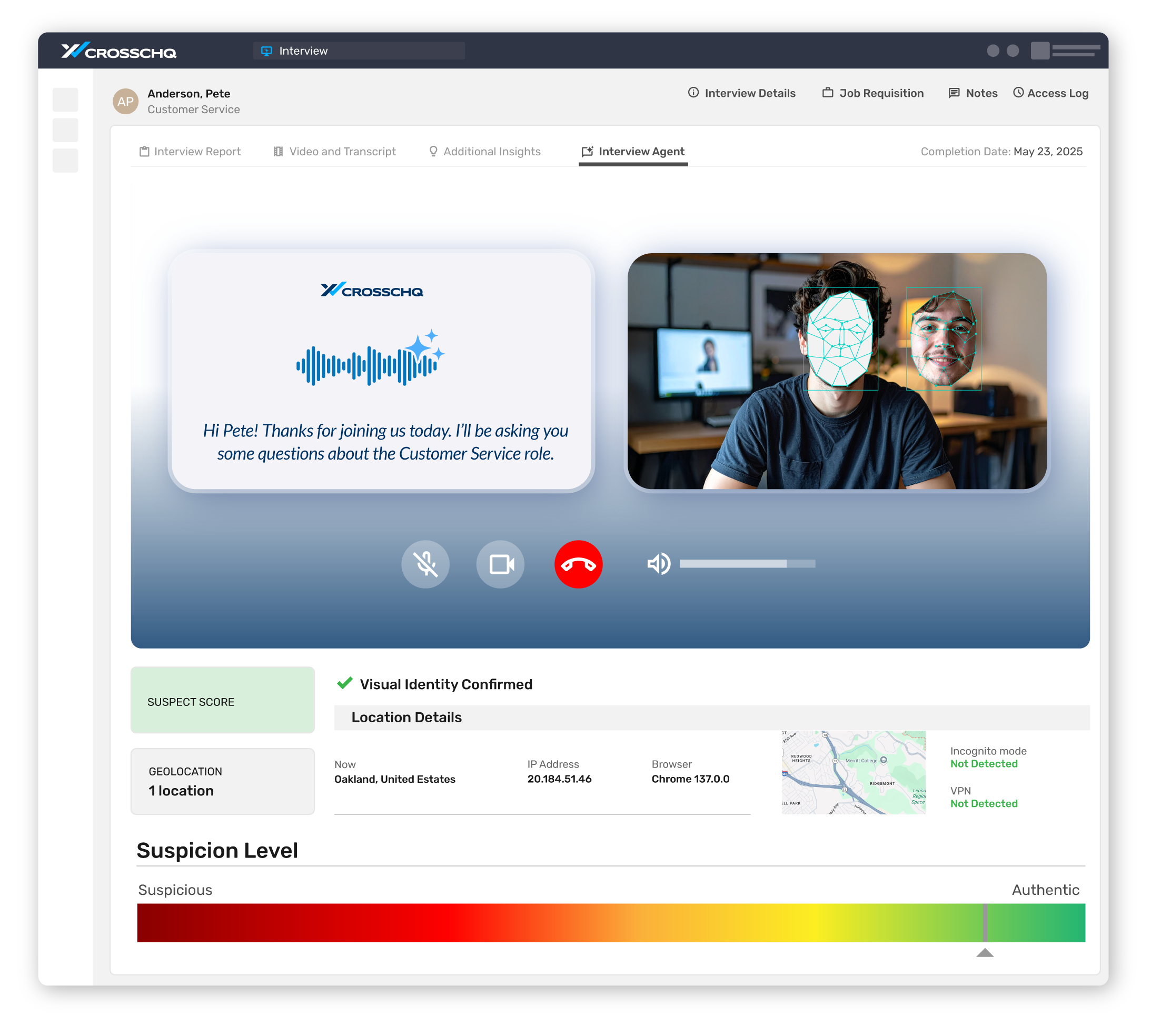
KEEP INTERVIEWS AUTHENTIC IN REAL TIME
Coming Soon! Guard against deepfakes and scripted/LLM answers during live conversations. When risk appears, an in-session alert agent notifies recruiters and suggests targeted probes. Assessment sessions are monitored for integrity, too.
Real-time authenticity + live guidance
Deepfake defense
Detect manipulated audio/video, voice clones, and face swaps during interviews.
Script/LLM detection
Spot generated or externally coached responses, unusual latency, and prompt artifacts.
In-session alerting
Guide interviewers with risk notifications and follow-up questions.
VERIFY IDENTITY BEFORE YOU INVEST
Confirm they are who they say they are with document and biometric checks, device/IP fingerprinting, and account-age risk signals. Catch synthetic identities and burner patterns early—before you spend recruiter time.

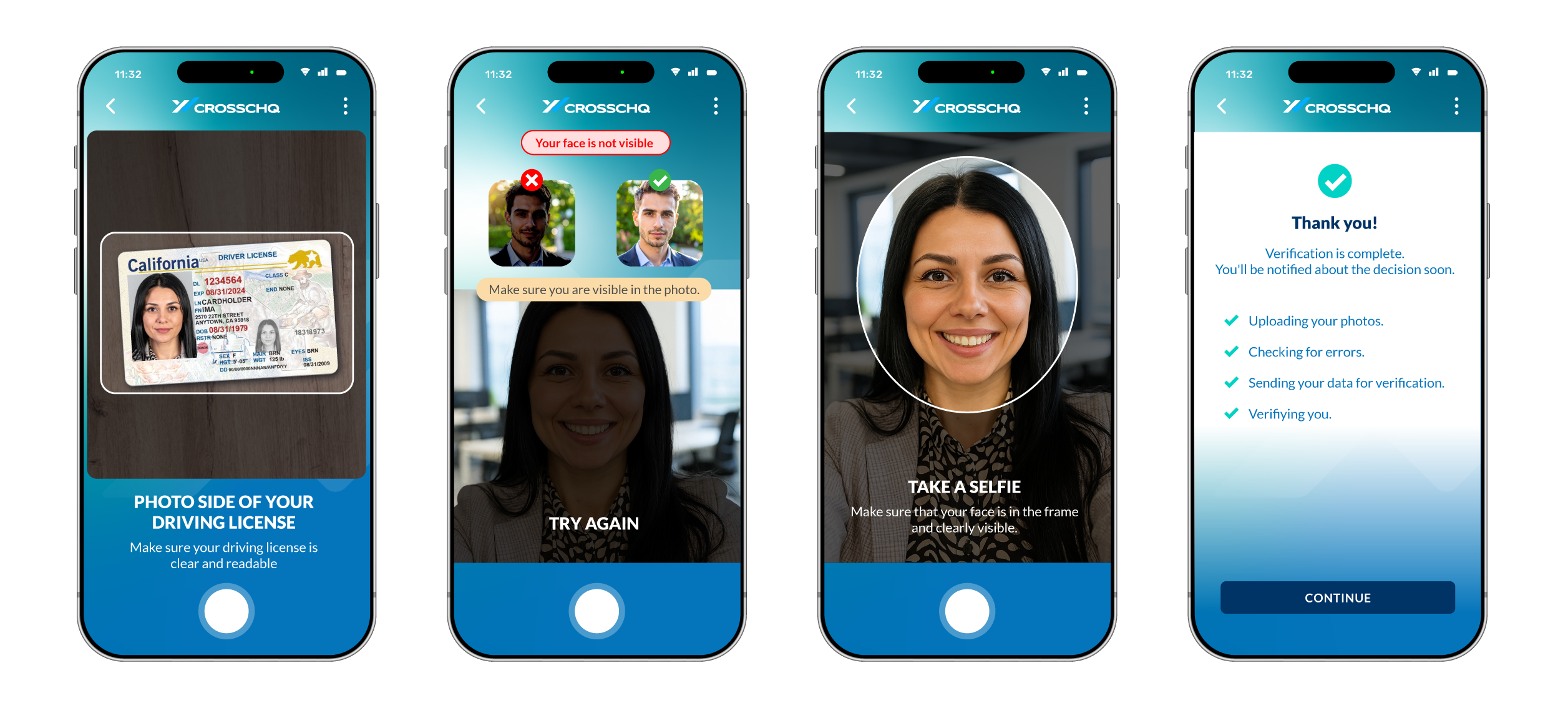
Trusted identity, fewer false starts
ID & biometrics
Validate government IDs against selfies and check biometric consistency.
Device & network
Match devices and IPs to reveal burner patterns and location anomalies.
Account trust signals
Score LinkedIn/email recency and integrity to flag synthetic identities.
.png)
VALIDATE REFERENCES —NOT JUST QUOTES
Confirm who’s vouching, whether they truly worked together, and if patterns suggest coordination or reuse. Network overlap and IP/device checks add another layer of confidence to every reference.
Reference intelligence you can verify
Identity & overlap
Confirm reference identity and employment overlap with the candidate.
Pattern & reuse
Detect templated responses, repeated contacts, and cross-submission reuse.
Network & device
Analyze social/pro network ties and track IP/device signals for inconsistencies.
Supercharge Your
Hiring Stack
Streamline your workflow with
out-of-the-box integrations delivering simple, frictionless experiences with the tools you already use.
.png)

4.9
4.8
4.7


Enterprise Grade
Security & Trust
Don't Let Fraud
Slip Through Your Funnel
GET A DEMO
%20-200x43.png)





